Why should you need to add security headers? Ensuring that your web application or websites are secured is very critical. In this metaverse time, securing user data and privacy is crucial, so as a website owner you should be safe and keep your users safe. In this article, I will share how you can add security headers to the OpeLiteSpeed web server.
What are security headers?
Security headers are directives that you define on your web server and according to these directives, web browsers can make it harder to exploit vulnerabilities such as Clickjacking or Cross-Site Scripting.
How to Add security headers to OpenLiteSpeed
Adding security headers on the OpenLiteSpeed server is easy, no need to use any command line. Simply log in to your web server’s admin console, and follow these steps to add security headers.
Security headers are a bunch of conditional directives that help secure your website. You can read in-depth the Web security section on MDN.
Select Virtual Host
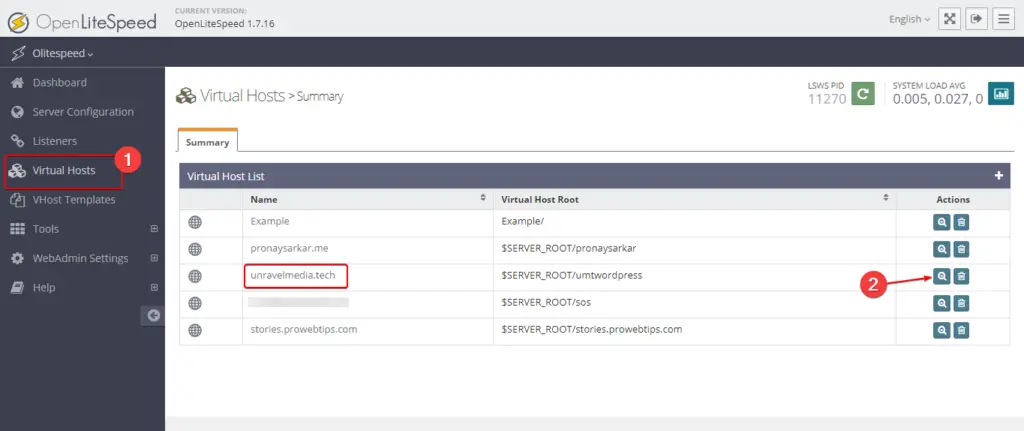
Add security headers for your website, which is hosted on the OpenLiteSpeed server. Login to the web admin console and navigate to the Virtual Host section, where you will find the list of Virtual hosts for different websites. Select the virtual host as shown in the image and navigate to the context menu.
Add Context with Security Headers
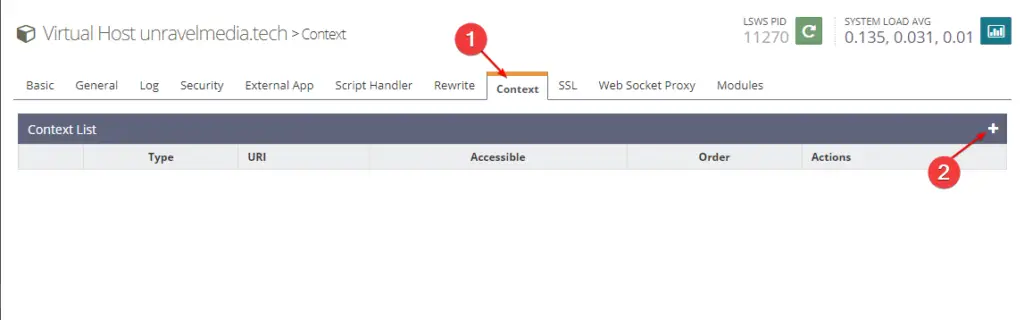
When you navigate to the context tab in the virtual host you probably won’t find any context in the list. Perhaps we have to add a new context, so as shown in the image above click on the plus (+) sign to add a new context.
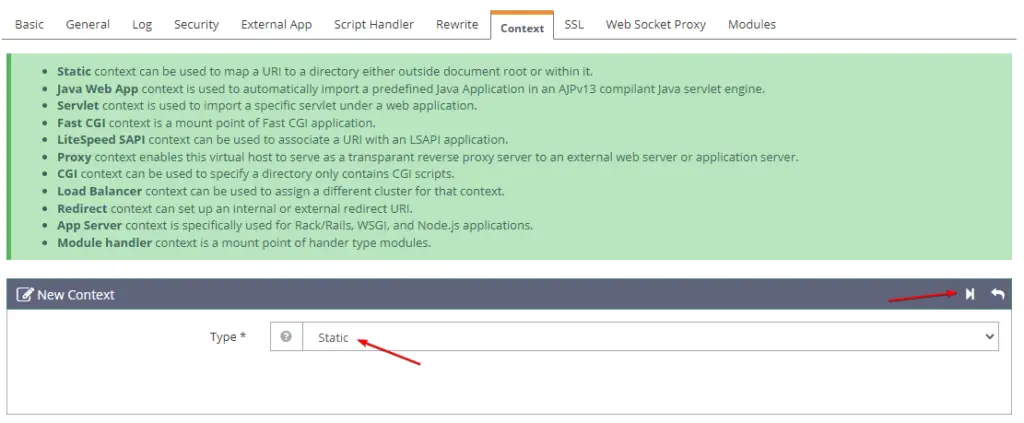
When you try to add a new context, the web server will prompt you, to what type of context you want to add, which you have to select from the dropdown options. In our case, need to select static as default in the image above, and then click on next.
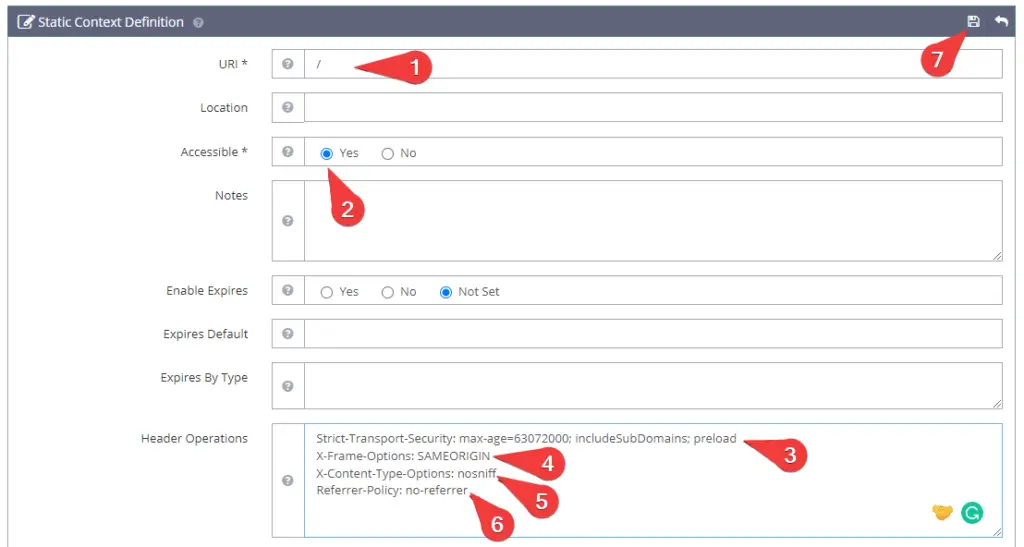
As shown in the image above you have to put relevant information including header derivatives. So, as I listed the information below, need to copy and paste them into your OpenLiteSpeed web admin console.
- URI: /
- Accessible: Yes
- Header Operations:
Strict-Transport-Security: max-age=63072000; includeSubDomains; preload
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
Referrer-Policy: no-referrer
Cross-Origin-Resource-Policy: same-site | same-origin | cross-origin
Cross-Origin-Embedder-Policy: unsafe-none | require-corp
Permissions-Policy: accelerometer=*, autoplay=*, fullscreen=*, picture-in-picture=*, web-share=*
Cross-Origin-Opener-Policy: same-origin-allow-popups
Content-Security-Policy: default-src * 'unsafe-inline' 'unsafe-hashes' 'unsafe-eval'So, you can copy these lines of code and paste them into your server.
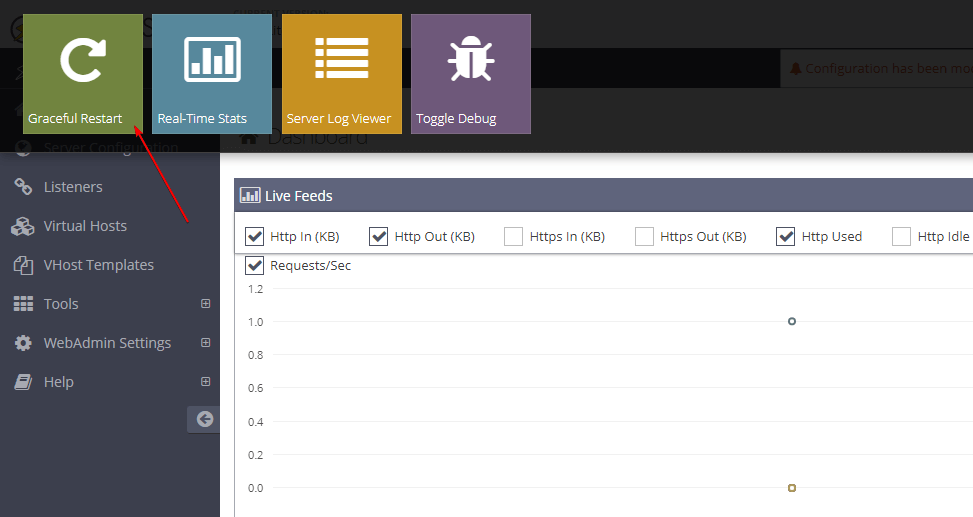
After saving the header operation derivatives, we have to restart the webserver to work. So, as shown in the image above, you have to do a graceful restart.
Check the security headers response
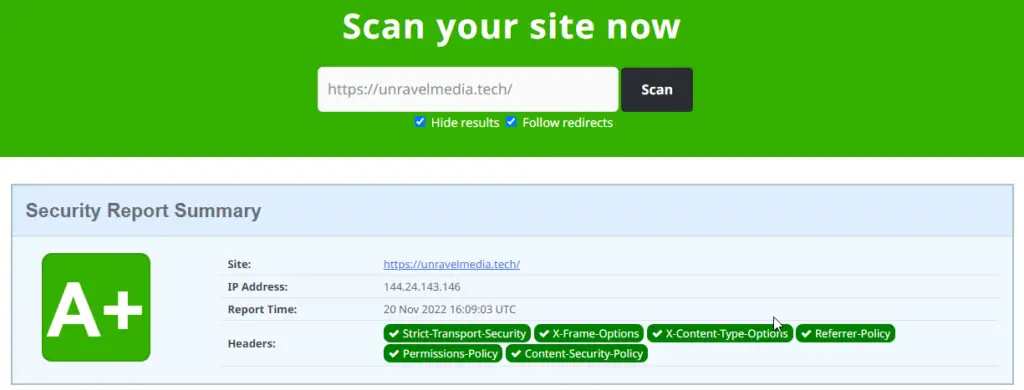
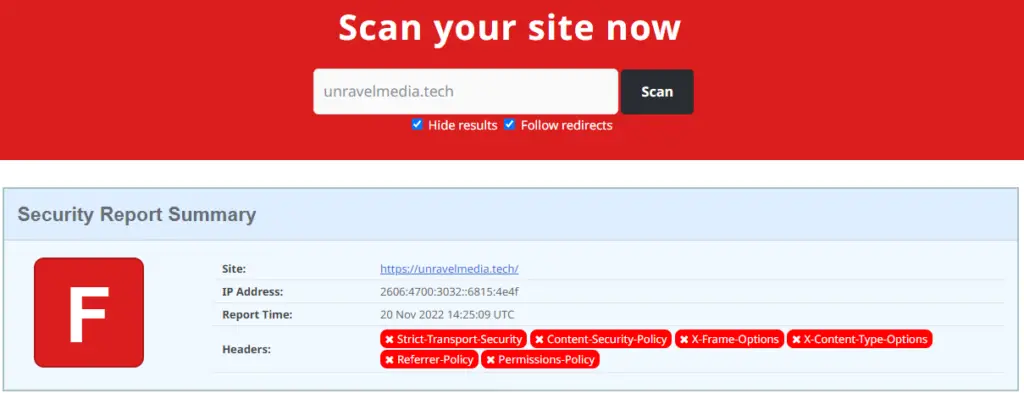
Visit https://securityheaders.com/ or use any security header scanner, it will tell you the header’s response, even you can use developer mode in your browser to check which header is working and of them causing any errors or not. Using the URL you can get your site’s security rating as shown in the image above.
Above these lines are just basic security derivatives, that we thought every site should have. However, every site has a different perspective and diverse user base so to protect your site you can also customize your way by researching online. However, I have explained these security derivatives, and what they do.