Log4j vulnerability is one of the greatest (critical severity) zero-day in modern times (2020). It is also known as the “log4Shell” attack. Log4j is a logging framework library widely used in applications and services.
Even as an individual log4j is almost certainly a part of the devices and services that you are online with every day. So, that answers the first question who is affected by this? Well presumably everyone whether you are an individual or an organization, this is going to affect you. This is a massive zero-day and turns out it affects a large variety of applications, a lot of the server-side and lots of them client-side.
Must Read: 9 Tips to secure your website from hackers.
But especially, things like Apache web server and that means every website (Which websites those are powered by Apache webserver) you visit could be potentially exploited by this vulnerability to make it worse.
In most cases, this is going to be a remote code execution (RCE) class vulnerability, which means it can be used to run any kind of software on your system remotely.
Once the attacker has gained access so they can remotely run any set of commands or applications on your system which includes ransomware, crypto-miner, malware, etc.
How to Check the system is log4j Vulnerable or not?
Log4j is an open-source framework and in the community, many people have been already made various scripts to detect vulnerable log4j versions, such as python-based log4j-scan and LunaSec from lunasec.io.
Here in this article, we are going to share a bash script, which is the very easiest method to detect log4j vulnerability, however, it’s not guaranteed that this script will ensure, you are 100% vulnerable or not, perhaps none of them. Our recommendation is that you must use all scripts and analyze them manually by yourself.
You can download the bash script and have to execute the following commands to identify the log4j vulnerability. For executing commands, you must have root privileges on your system.
wget https://raw.githubusercontent.com/rubo77/log4j_checker_beta/main/log4j_checker_beta.sh -qchmod +x log4j_checker_beta.shsudo ./log4j_checker_beta.shNote: - Downloading scripts from the internet and running them as root could be harmful to the system, so please be careful and analyze before you download things from the internet. Perhaps, this script we have used to identify vulnerability on our system and it’s safe.
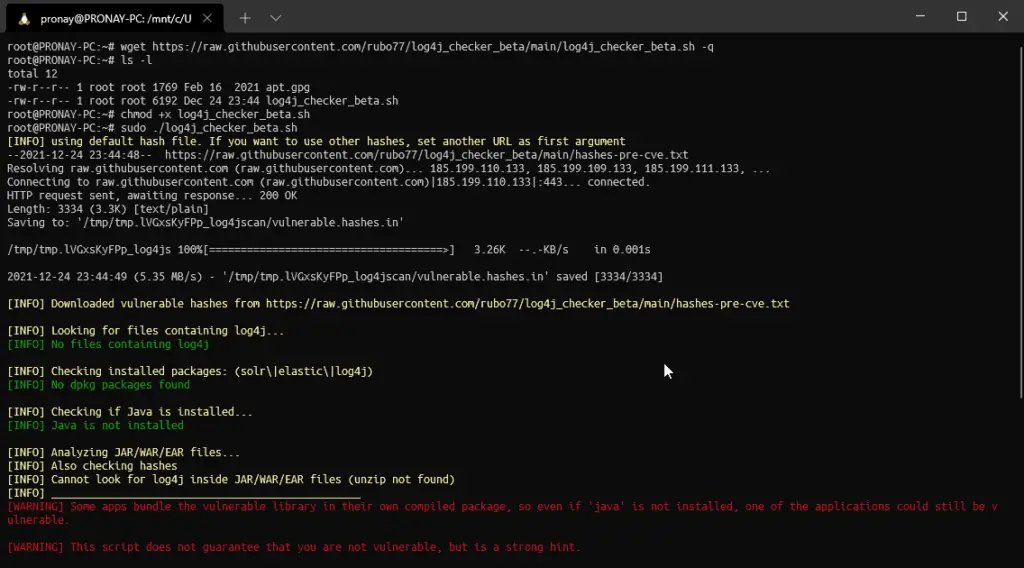
As you can see in the image, we execute the bash script to find log4shell vulnerability, but the script doesn’t find anything. Again, this script doesn’t find anything that means you are not vulnerable, that is not guaranteed. Perhaps you must check out other scripts or just find them manually by yourself. Even you can use the find command on your Linux system to manually identify the vulnerability.
Some applications come bundled with Apache log4j library, and if you are thinking you haven’t installed any application and you are not vulnerable, it would be wrong thinking. You must check the system and if any applications using log4j library version 2.0-beta9 to 2.16.0, excluding 2.12.3 then you must replace it with a newer updated version.
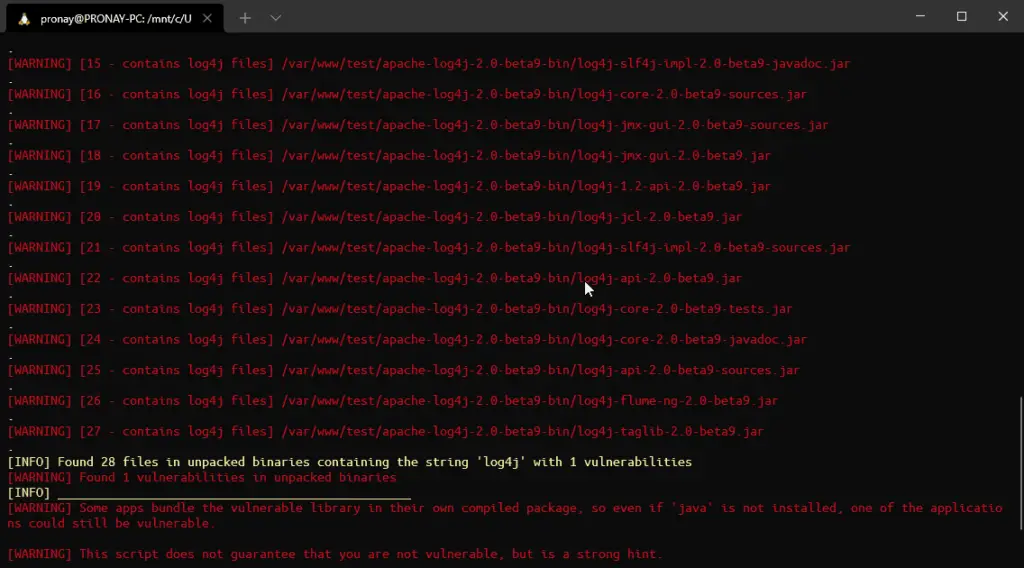
As you can see from the image, we run the second test and for that, we had downloaded the vulnerable log4j version 2.0-beta9 from the Apache archive. It was in zip format, for testing purposes we unzip it and run the bash script to identify the log4shell vulnerability, and you can see the result on the image.
System is Vulnerable, how to patch?
If your system is vulnerable with this zero-day, then you wondering how to patch it? The whole open community working on the issue, and to date Apache released three and more updates regarding this. If your system is affected by this log4shell vulnerability or your system has the affected version of log4j library 2.0-beta9 to 2.16.0, excluding 2.12.3, then you must update the latest library package.
You can replace them or simply follow the official Apache mitigation procedure. If you are using the Windows system, then follow the official article from Microsoft.
How to be safe from being attacked by log4shell or any vulnerability?
The famous proverb probably you heard, “Prevention is better than cure,” if you got attacked that means you haven’t taken “Security” seriously, and not hardened the system with standard security policies. And you must also keep eye on the news, everyday new zero-day get identified and according to your system, you must take action.
There are some security tools, like CrowdSec, Fail2Ban, pfSense, and more, you can use to improve security hardening on your Linux system. Specially CrowdSec working with the community to prevent log4shell exploitation. But if the system has a vulnerable log4j library then it must be updated to the latest version.
In case you are a home or individual user and using a Windows system then our recommendation is to use a good anti-virus tool to prevent any vulnerability or ransomware attacks.
FAQs about Log4j library
What is the log4j?
Apache log4j is a popular logging service framework and it has been widely adopted and used in various applications.
Is my WordPress website is affected by the log4j vulnerability?
It depends, WordPress typically doesn’t use the log4j library for logging services. However, if your server has any application that uses the log4j library, then your whole system including the WordPress site could be vulnerable.
I am using shared hosting, could be I vulnerable with log4shell?
Yes, but by now your hosting provider probably fixed the vulnerability. For more information, you must contact your host provider.
Conclusion
Apache log4j is a very popular logging service and is widely used in applications. If you are using log4j library version 2.0-beta9 to 2.16.0, excluding 2.12.3, then do upgrade with the latest version. These specified versions are identified as security vulnerabilities CVE-2021-45105, CVE-2021-45046, and CVE-2021-44228.